What is intelligence ?
Intelligence is a fascinating concept as an invisible force that propels us forward, helps us solve problems, and understand the world around us.
It's not just about book smarts or exams; it's also about being streetwise, and knowing how to handle different situations. And the coolest part? It is not static. We can always learn more, expand our horizons, and increase our intelligence. If you are an information security professional, it is very important to improve your intelligence about ongoing or anticipated threats in the cyber world.
What is Threat Intelligence ?
Threat Intelligence is evidence-based knowledge of existing or emerging threats or hazards to assets. It includes context, mechanisms, indicators, implications, and useful advice. In the field of cybersecurity, threat intelligence plays a key role in understanding the motives, goals, and offensive behavior of threat actors.
Here's why it's important:
Proactive decision-making: Threat intelligence enables security teams to make informed decisions by shedding light on the unknown. It allows them to adjust defenses proactively rather than reactively.
Understanding Adversaries: By revealing adversary motives, tactics, techniques, and procedures (TTPs), threat intelligence helps security professionals better understand the decision-making processes of threat actors.
Business Empowerment: Threat Intelligence is not just for technical teams. It also enables business partners – executive boards, CISOs, CIOs, and CTOs – to invest wisely, mitigate risk, and make decisions faster.
Whether you're a small business or a large enterprise, leveraging threat intelligence can significantly strengthen your security posture.
Cyber threat detection is a closed loop and consists of six key elements. These elements carry information to the next part of the process and are all dependent on their previous step. Any kind of intelligence can be processed through this system.
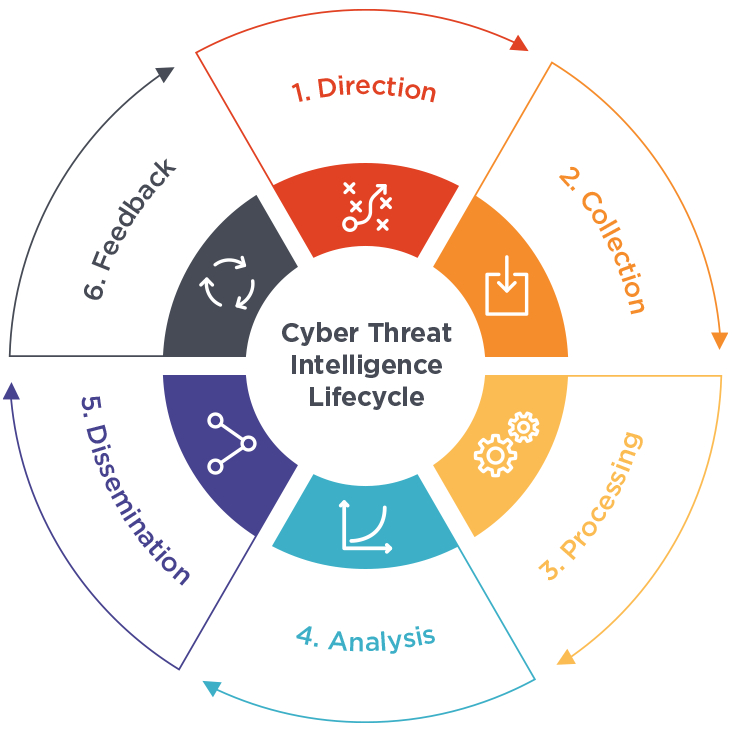
- Direction
- Collection
- Processing
- Analysis
- Dissemination
- Feedback
- Direction: The first step is to define what information is needed to make informed decisions in the shortest possible time frame. This helps define targets that are based on evidence gathered, such as the nature of the attack, the devices used, and what was compromised.
- Collection: Data collection can consist of digital and physical evidence depending on the incident. This can include audit logs, IP addresses, CCTV footage, or even physical devices, depending on the nature of the attack. At large scale, data collection can exceed terabytes of space, which means proper planning, storage, and processing will need to be considered.
- Processing: The raw data is then processed into more organized decipherable forms. This may involve literally decoding information, organizing raw data into groups, or labeling information that is relevant to a specific context or source.
- Analysis: Based on the data collected, a timeline needs to be established and conflicting information needs to be further analyzed and compared to better understand the events as they unfolded. At this stage, patterns and other evidence may emerge that require even further analysis. This is often one of the most time-consuming phases of the cycle and is almost always led by a human analyst and assisted by other tools.
- Dissemination: The messages generated from the analysis phase must reach decision-makers so that action can be taken.
- Feedback: An action is performed based on all previous steps in the cycle. This could involve retaliation, the implementation of a new security feature, or it could be in the form of adding more data to the cycle for rechanneling. Once feedback is provided, the process begins again.
